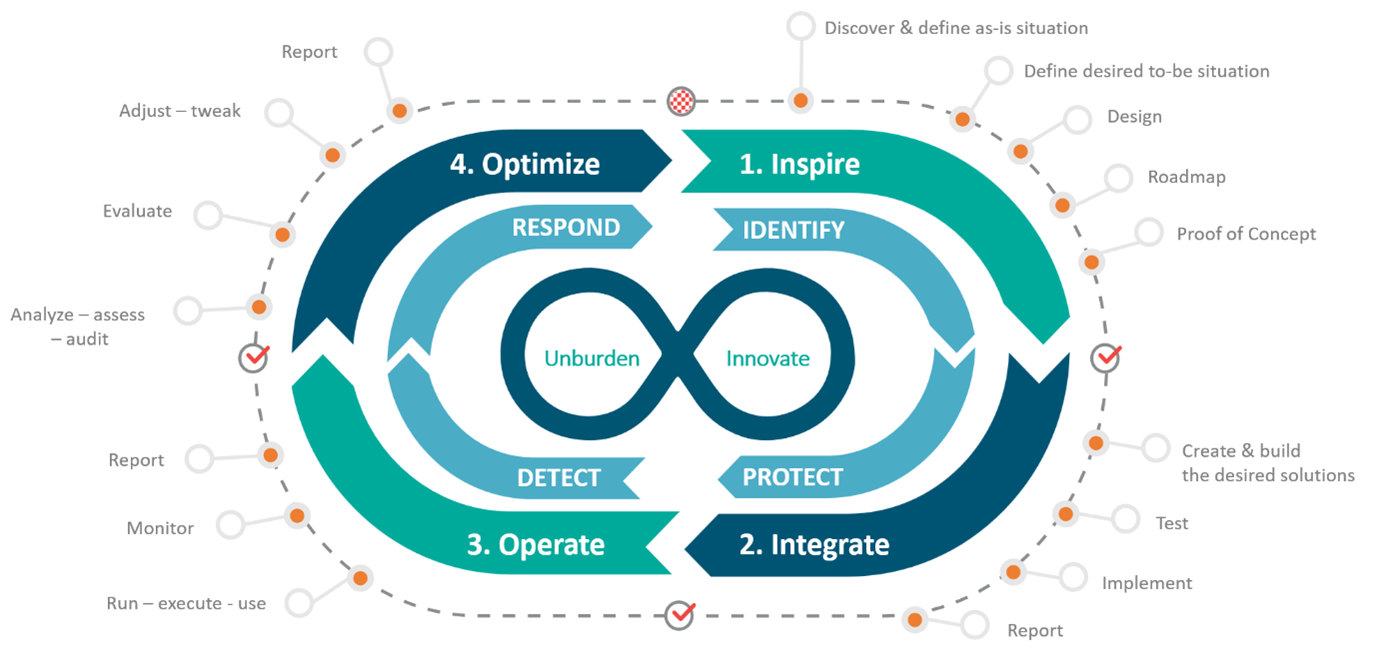
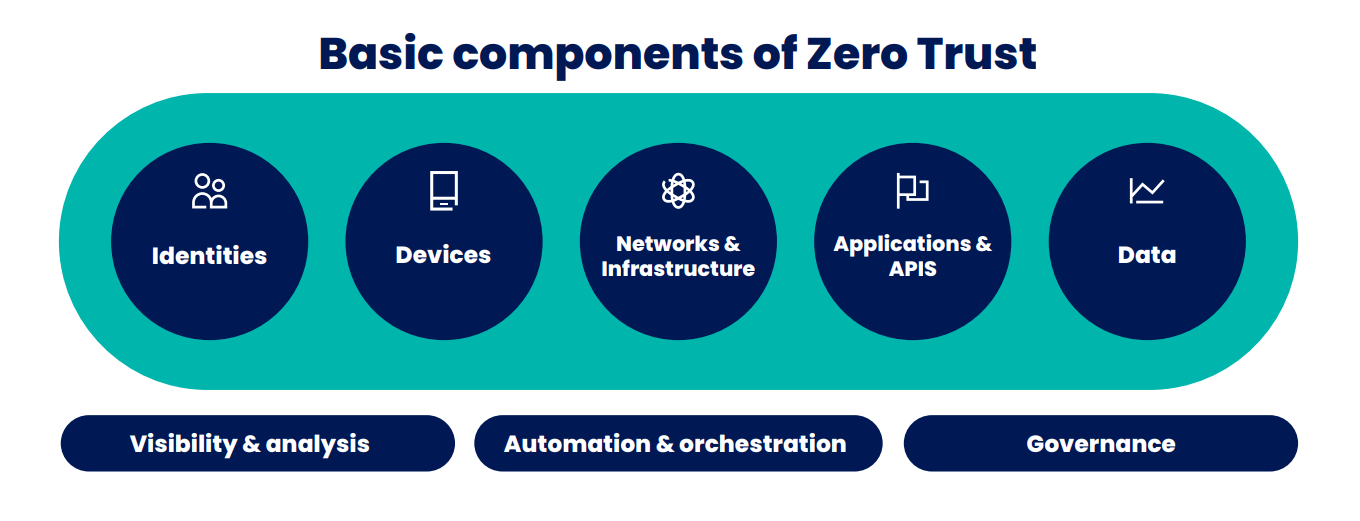
Your users are becoming increasingly mobile, IT environments are becoming more complex, and threats are constantly evolving. As your data, applications and users become more diffuse, securing your data is becoming increasingly challenging. Cyber attacks can happen at any time and criminals are becoming increasingly innovative. Is your company sufficiently secure? Can you respond quickly and efficiently in the event of an attack? Can you still keep up with the latest developments?
Our vision is that cybersecurity isn't just a matter for specialists – it concerns all of us. Implementing a solid cybersecurity strategy tailored to your organization's size, risks and business challenges is essential. If you are finding it difficult to keep up with developments, we will be happy to help you implement an effective strategy.