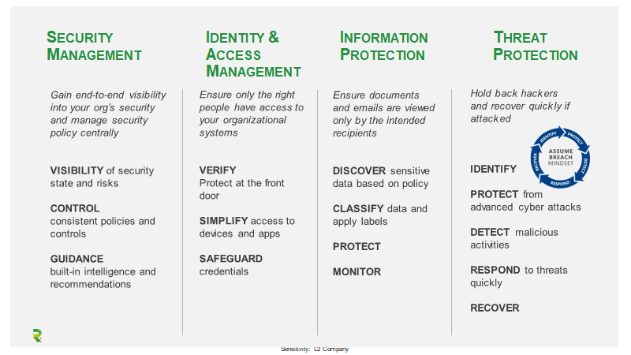
Microsoft Information Protection (MIP)
MIP is Microsoft's name for a range of solutions that can help discover, classify and protect or restore sensitive, personally identifiable information, wherever this information may be: locally, in the cloud, on a device or in an app. Such means of protecting confidential information can be particularly useful in ensuring compliance with legal requirements such as the GDPR.
In practice, these resources allow you to monitor who has received or opened certain files, at what times and on which devices. You can also use them to detect policy violations and risky behavior and to investigate trends. To protect sensitive, high-risk files, you may choose to encrypt them. You can also act remotely to block access to these files, regardless of how many copies have been made.
Microsoft Identity & Access Management (IAM)
Microsoft EMS offers an efficient, secure identity management platform, ensuring that the right people (such as employees and partners) are authorized to access the right files and environments. Azure RMS and Windows RMS (Rights Management Services) are familiar elements, but the most popular feature may well be the option to set up a Conditional Access policy. In addition to checking from which location someone has logged in and on which device, you can also implement rules and procedures to control which devices may access your various services and data sources.
To further protect the identity of your users, you can make use of one of Microsoft IAM's many multi-factor authentication (MFA) options. This way, logging in will require an additional verification step, such as a security code that is sent to your mobile phone by text message. The pricier subscription plan even allows you to automatically block accounts or make users change their passwords if the system has detected abnormal activity. You can also locate specific devices.
Of course, the main thing is to restrict access to unauthorized individuals and criminals without hampering your own employees' productivity. In certain cases, it may therefore be advisable to use a single sign-on (SSO) with one, strong password. If your employees only need one click to access all your apps, both on-premise and in the cloud, they won't have to remember passwords for all those different accounts.
Microsoft Advanced Threat Protection (ATP)
Finally, Microsoft offers a number of ATP solutions to further protect your assets and optimize your general security, such as Office 365 ATP, Microsoft Defender ATP and Azure ATP. These focus on document and device security and identity and access management, respectively. Office 365 ATP, for example, allows you to proactively remove dangerous links and attachments from emails.

Last but not least, this category also includes Azure Sentinel, a cloud solution for Security Information & Event Management (SIEM). It provides you with a general overview of different data sources and security applications, including those from other suppliers. While each application concentrates on its own domain and may not be aware of threats outside that particular area, Sentinel's overview keeps you informed. You can read more about managing security for all your workloads in the cloud with Azure Security Center and Sentinel in an earlier blog post. Those of you who want to know all the technical details can also watch a recording of our webinar.
Want to know more about how M365 can enhance your security?
We offer various Cloud Security Workshops to help you with your security approach, based on Microsoft 365 Security or a security cloud journey. Contact our experts at an.depreter@realdolmen.com. Of course, you can also get in touch with your regular Realdolmen account manager.
 Microsoft 365 (M365) combines two familiar and popular solutions: the Windows 10 operating system and the cloud-based office suite Office 365 (O365). To cap that off, Microsoft has also added a complete security suite, EMS (Enterprise Mobility + Security). That's certainly a useful addition as these days, companies seem increasingly unaware of where their data is actually located: locally, or in the cloud? Nor do they always know the provider.
Microsoft 365 (M365) combines two familiar and popular solutions: the Windows 10 operating system and the cloud-based office suite Office 365 (O365). To cap that off, Microsoft has also added a complete security suite, EMS (Enterprise Mobility + Security). That's certainly a useful addition as these days, companies seem increasingly unaware of where their data is actually located: locally, or in the cloud? Nor do they always know the provider.

